Of Course I Can Recognize Spam! Can’t everyone recognize spam? By definition spam is unsolicited bulk messages sent through email. “Great, I have a definition now, but how does that help me?” Unsolicited, in this case means you have not had any interaction with this company, brand, or person. In other words, someone got your email address […]
Category Archives: Continuing Education
We covered what a Managed Service Provider is in our last article. Now it’s time to take a deeper look into how an MSP protects your organization. Let’s start with what your people notice the most, the PC at their desk and the software that runs on it. Both hardware and software are in need of continual updates and […]
Every day is a good day for computer security, but today is all about raising additional awareness about you and your computer’s security. Let’s get right to it! #1 You are a target. You may not be a corporation, or have a lot of money, but you are still a target. It might be a password, personal […]
Basic Online Safety for Working Adults Basic online safety The internet and the online world can be accessed from anywhere thanks to wireless technology. But as beneficial as the internet can be, the words of Obi-Wan Kenobi must be heeded, “You will never find a more wretched hive of scum and villainy. We must […]
How Antivirus Works Antivirus software is a multi-layered security strategy that is easy to apply to your devices. Antivirus runs in the background, happily defending you from malware and viruses as you go about your day. So, how does it do that, exactly? Traditional Method Traditional antivirus products use a series of signature files. Their […]
First off, let’s explain what a cyber attacks and ransomware are. They are any type of offensive maneuver that targets computers, networks, and infrastructures by various means of malicious acts designed to steal, alter, or destroy data or targeted systems. Recently, ransomware has become the poster child for attacks. It is designed to infect a pc […]
Quick Steps in Outlook Quick Steps is a new feature in Microsoft Outlook that applies multiple actions at the same time to email messages, similar to Rules. They help you quickly manage your mailbox. For example, if you frequently move messages to a specific folder, you can use a Quick Step to move the message […]
Function Keys Do Something? The F1 – F12 keys at the top of your keyboard do have functions and it differs a little depending on what operating system you are using. Windows and Mac are going to be different. Today we are focusing on Windows functions, since the bulk of you use that day to […]
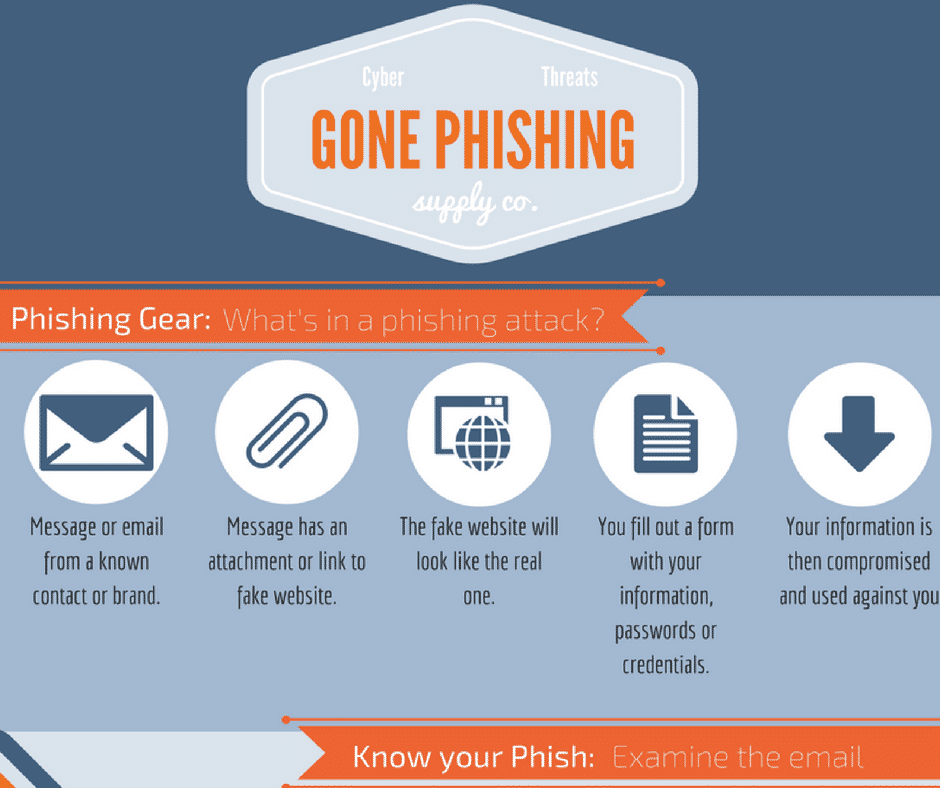
What is Spear Phishing? Spear Phishing is the practice of sending emails ostensibly from a known or trusted sender in order to induce targeted individuals to reveal confidential information. Fancy words for a hacker sending an email to trick you into giving out your passwords or other information that could compromise your data, bank accounts, or […]